1.What is “Source code auditing” ?
代码审计也即白盒测试,通过给出的源码寻找漏洞。现有的方法包括污点分析等。本文主要介绍最原始最朴素的人工代码审计方法以及高危函数。
2.Skills of Source code auditing
- Look at the big picture
- Audit functions you know are unsafe
- Printf, strcpy, gets
- Make a list of interesting functions as you audit
- Try to understand what a function does by its name first
- Don’t jump between functions too much, you’ll confuse yourself
- Bottom up approach
- Start at user input
- Move up and see where your data goes
- Read the manual
3.Vulnerable types
- Bad API usage
- Think memset, strncpy(dst, src, strlen(src))
- Format strings
- Gets
- Leaking stuff with strncpy (it doesnt set a NULL byte)
- Heap
- UAF / Double Free / Custom malloc implementations
- Logic bugs
- Integer overflows / Underflows
- Can lead to buffer overflows in the future
- Or incorrect program state
- Type conversions
- Converting between char and an int
- Signed to unsigned
- Pointers to flow … etc
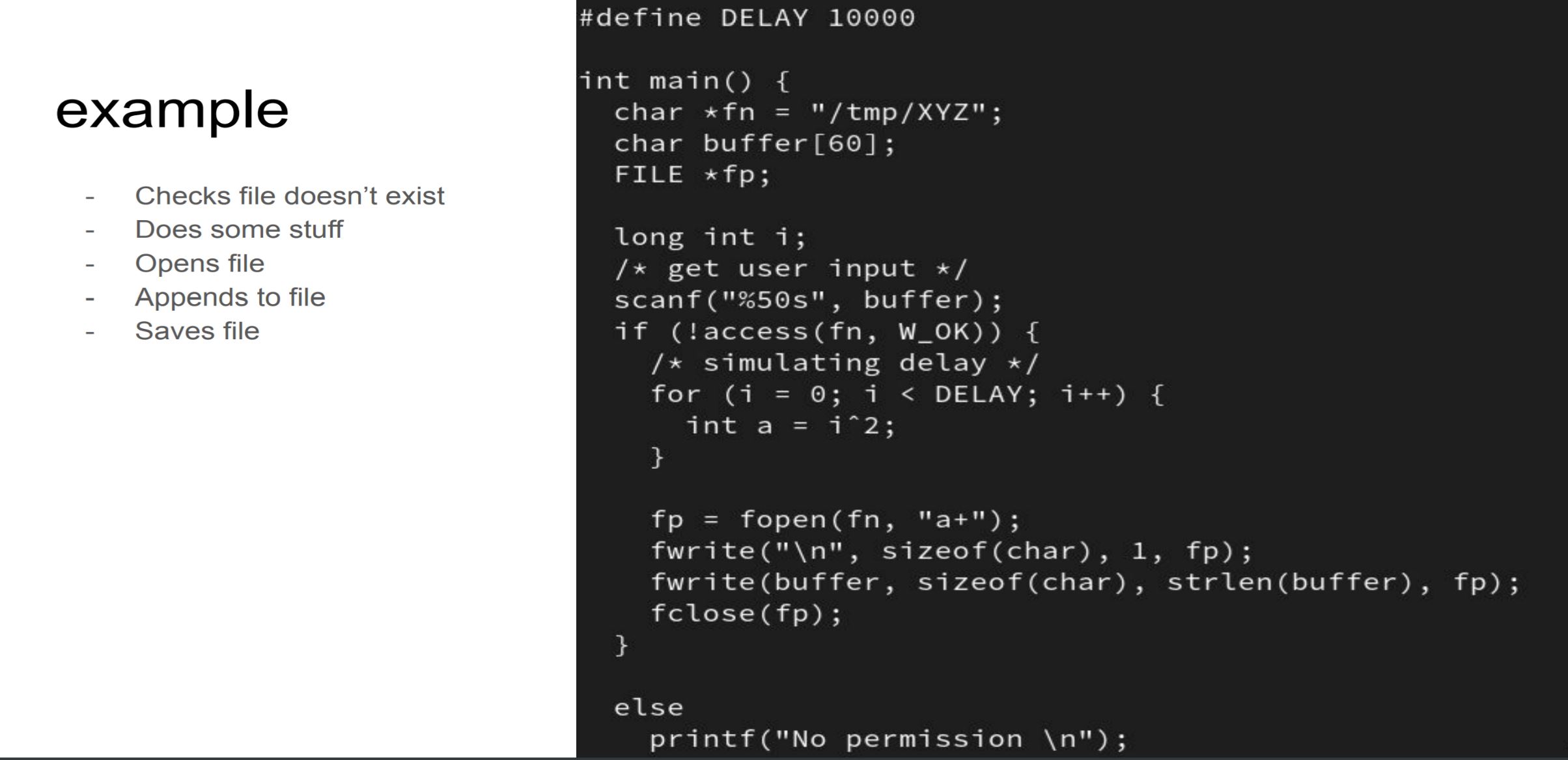
4.Vulnerable function
-
fmt_vuln
- printf
-
bof_vuln
- gets
- strcpy
- strncpy
-
Heap
- UAF
- free
- Double free
- free
- UAF
-
Integer overflows and underflows
- sizeof()
- int length, length + 1
-
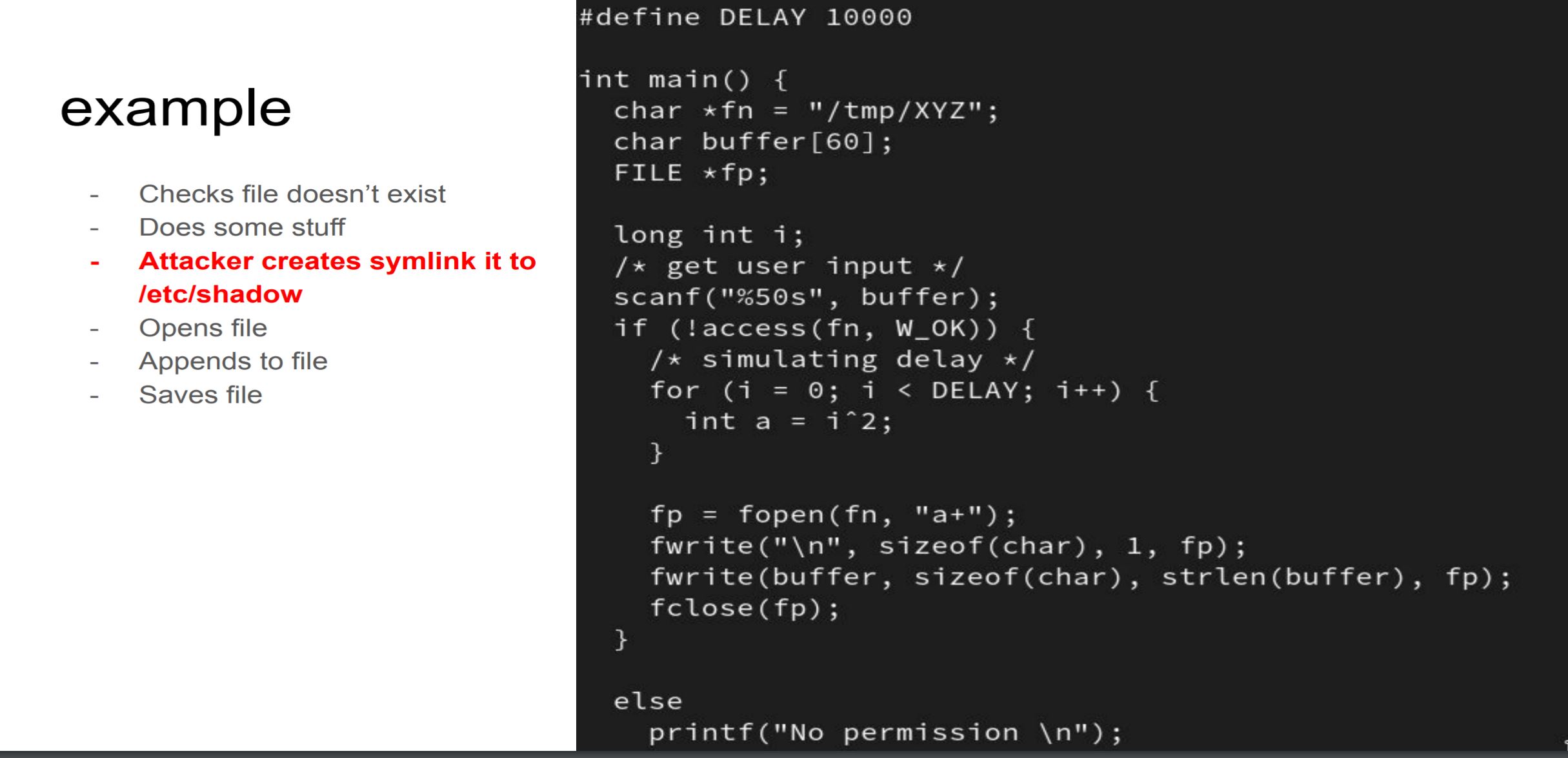
Race condition
- A race condition is a generic situation where two or more actors are about to perform an action, and the result depends on othe order in which they occur.
- A race condition is a generic situation where two or more actors are about to perform an action, and the result depends on othe order in which they occur.
5.PWN Vulnerable function
-
Integer Overlow Vulnerability
- int len
-
BOF vulnerability & Arbitrary Leak On Heap Vulnerability
-
fputs()
-
read()
buffer = calloc() printf()
-
-
Format String Vulnerability
- syslog() #snprintf 会确保生成的字符串以 \0 结束
-
User-After-Free vulnerability
- free()
-
Rce vulnerability
- system()
-
Potential log truncation risk
- snprintf()
-
Directory Traversal Vulnerability
- snprintf()
- file = fopen()
-
Memory Leak Vulnerability
- strdup()
-
Arbitrary Free vulnerability
int id = 0; if (id >= len) { puts("Chunk not allocated"); exit(0); } free(chunks[id]); -
Stack Overflow vulnerability
- alloca() #分配函数在栈上
-
Uninitialized Buffer
buf[max_size] fread() -
Memory Leak
- calloc()